Performance
Ultra-fast, reliable cloud object storage with 13 global region + On-Demand Direct Access for AI/ML workloads.
Know more
Protection
Eleven 9s data durability. Immutable storage with object lock.
Know more
Veeam®
Veeam® with IDrive® e2 - save 90% in storage costs.
Know more
MSPs and Resellers
Buy storage for your MSP needs or resell at your price.
Become a Reseller
Cloud Migration
Switch to IDrive® e2 from your existing storage provider with FREE cloud migration.
Know more
IDrive® e2 Features
Cloud Object Replication
Replicate data across regions for enhanced redundancy, compliance, and faster local access.
Event Notifications
Configure event triggers for specific buckets and receive instant notifications when files are added, modified, or deleted.
Bucket Logging
Track requests, monitor access, and enhance security with detailed logs.
On-Demand Direct Access
Secure, on-premise IDrive® e2 deployment for reduced RTO and optimized RPO.
Ransomware protection
Protect against data loss from malware attacks with file lock, versioning, data retention.
Object lock
Object locking brings immutability to the objects and protects your data from cybersecurity threats and maintain regulatory compliance.
Bucket versioning
Previous object versions are retained based on the bucket retention policy. Retrieve objects in case of accidental overwrites or deletion.
Edge locations
Create a storage near your end-users for faster network and ease of access.
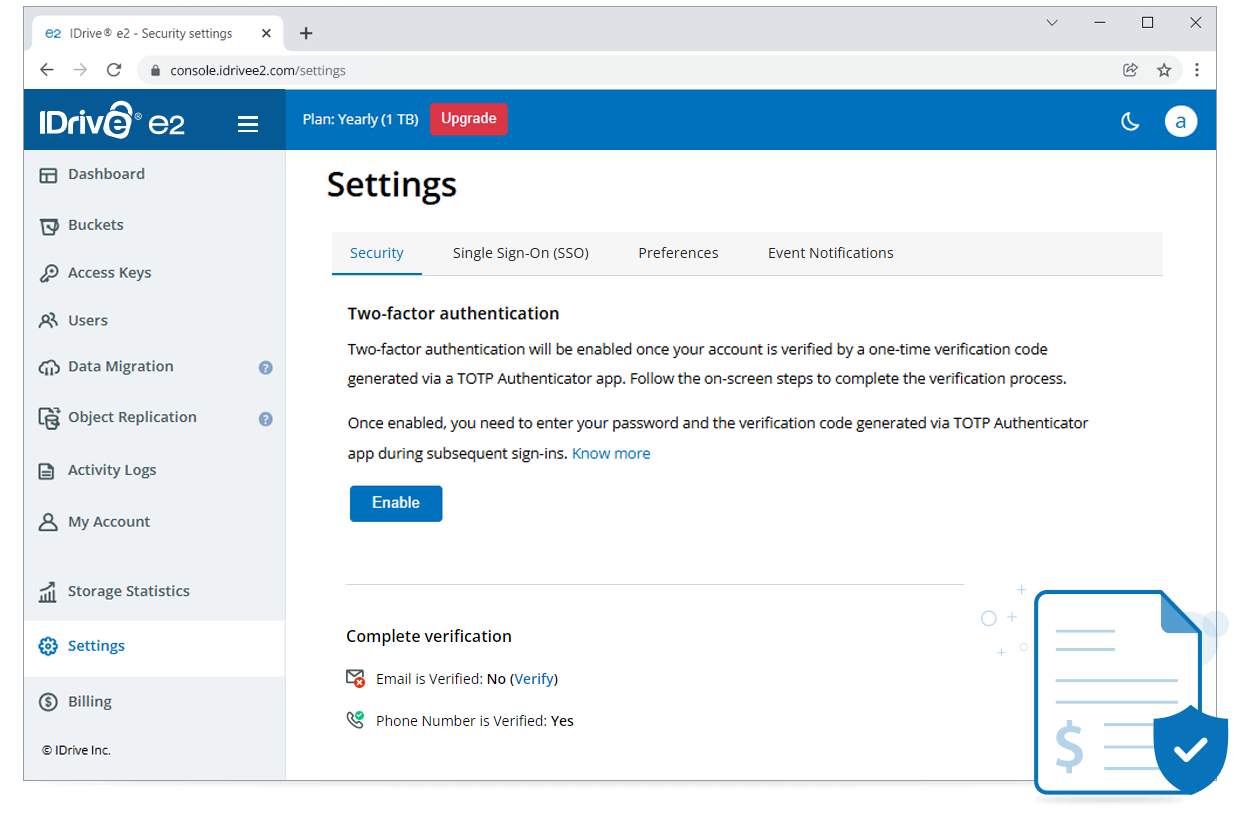
Multi-factor Authentication (MFA)
MFA enhances account security by requiring an additional layer of verification—a time-based authentication code generated on a trusted device. Access to the account, as well as permissions to delete objects of MFA enabled buckets, is granted only after successful verification of this code.
Encryption and privacy
Data is stored in data centers with physical and biometric security, and all transfers are secured with TLS protocol and offers encryption at rest.
Centralized access
Access, manage, and restore data from anywhere via an easy-to-navigate web-based console.
IDrive® e2 Public Buckets
Set up public access for your IDrive® e2 buckets and manage access permissions for your public data.
Cloud Data Migration
Move data directly from other cloud storage providers to IDrive® e2 at no additional cost or tool requirement. IDrive® e2 offers cloud data migration for FREE.
Data Lake Storage
Store massive volumes of raw data - structured, semi-structured, or unstructured - affordably in IDrive® e2 hot object storage.
Multi-cloud compatible
Build a flexible, robust, and portable multi-cloud infrastructure with reduced costs, enhanced performance, integration support, and data security features.
IDrive® e2 for Snowflake
Snowflake users can store data on IDrive® e2 and use it to create Snowflake database tables. They can also store Snowflake External stage and External tables.
IDrive® e2 with MSP360
Configure IDrive® e2 hot cloud object storage with MSP360 backup software and store your data affordably and securely.
The cloud storage that meets all your needs
IaaS
Store application data in distributed endpoints that are closer to your users. Run APIs, development kits, and services over a geographically-connected network of servers.
Data backup and archival
Safeguard your organization's systems, servers, NAS devices, VMs, Veeam, and workstations by storing the data in the cloud. Transfer data from local storage or another cloud storage.
Manage media workflow
Store petabytes of photo, video, and audio files from the cloud without making changes to your workflows. Archive active and inactive media workflow with your preferred media management tools.
AI/ML Projects
Store large data sets affordably in the cloud. Implement artificial intelligence and machine learning systems to analyze, learn, and predict from the data.
Video surveillance
Access, manage, and secure data from CCTV systems, IP cameras, NVRs, and VSaaS platforms with scalable and affordable, hot cloud object storage.
Compatible clients to use with IDrive® e2
Automate regular backups of your Google Workspace data for all users to the cloud.

Secure data across Microsoft Office 365 apps with automated regular cloud backups.

Safeguard your Drive and Team Folders data with 3 times daily automated backup.

Keep your Drive data safe from loss and ransomware by backing up to the cloud.

Transfer your backed up data to IDrive® e2 via Veeam Backup and Replication tool.
Integrate Veeam Kasten with IDrive® e2 to enable scalable, efficient cloud storage for secure Kubernetes data protection.
Use MSP360 CloudBerry to mount your cloud storage as a network drive to your Windows workstation or Windows Server.
Use MSP360 CloudBerry Explorer to access, move, and manage files between your local storage and IDrive® e2 Cloud Storage account.
Integrate MSP360 Managed Backup Service with IDrive® e2 for secure, efficient, and scalable cloud backup management.
Integrate IDrive® e2 cloud storage with Adobe Premiere Pro using LucidLink.
Integrate Ahsay and store your data in the IDrive® e2 cloud.
Integrate Acronis Backup Gateway with IDrive® e2 to add scalable, secure object storage specific to Acronis environments.
Acronis Cyber Protect Cloud with IDrive® e2 to data backup with AI-based antivirus, anti-malware, and endpoint protection.
Integrate Actifio with IDrive® e2 to use it as a scalable cloud object storage repository.
Integrate ActiveImage Manager with IDrive® e2 to backup volumes or files to the cloud, enhancing data protection.
Integrate AirLiveDrive with IDrive® e2 to access cloud storage as a local disk drive.
Integrate AJC Sync with IDrive® e2 to seamlessly sync and backup local files to the cloud with improved availability.
Integrate Alluxio with IDrive® e2 to combine high-speed data caching with a capable object storage for AI workloads.
Streamline your workflow and collaboration with IDrive® e2 and Anchorpoit integration.
Integrate Ansible with IDrive® e2 to automate data workflows and cloud storage operations.
Integrate Apache Iceberg with IDrive® e2 using Apache Spark to enable scalable, secure cloud object storage.
Integrate IDrive® e2 with the Aparavi Platform to automate data workflows using secure, scalable cloud storage.
Secure your media files by integrating IDrive® e2 hot cloud storage and Archiware P5.
Create a secondary repository for your arcserve data in the IDrive® e2 cloud storage.
Replicate your Arcserve ShadowProtect backup images to IDrive® e2 Hot Cloud Storage.
Configure Arctera Backup Exec to use IDrive® e2 as S3 cloud storage, create and run backup jobs (Full/Incremental).
Configure and manage your backed up data on IDrive® e2 cloud storage using Arq.
Integrate Asigra SaaSAssure with IDrive® e2 for scalable, secure, cost-effective SaaS data backup and cloud protection.
Integrate Atavium with IDrive® e2 to unify data lifecycle management utilizing a secure, scalable cloud storage.
Integrate Atempo Miria with IDrive® e2 for scalable and cost-effective cloud backup, archiving, and data management.
Integrate Atempo Tina with IDrive® e2 to enable scalable, secure, and efficient cloud backup and recovery storage.
Integrate Ava Cloud Cameras with IDrive® e2 to enhance video storage with scalable and cost-effective object storage.
Integrate AvePoint Opus with IDrive® e2 to automate data lifecycle management while using a scalable object storage.
Use BackupAssist with IDrive® e2 hot cloud storage to store data backups from physical and virtual Windows servers.
Integrate BackupAssist ER with IDrive® e2 to secure Windows servers with a scalable and cost-effective cloud storage.
Integrate BackWPup with IDrive® e2 to secure WordPress backups with scalable, reliable, and cost-effective cloud storage.
Integrate Beluga CDN with IDrive® e2 to accelerate content delivery using a secure and scalable cloud storage.
Integrate BitMovin with IDrive® e2, utilizing a scalable, secure, and cost-effective cloud storage for video workflows.
Integrate BucketAnywhere S3 with IDrive® e2 employing a scalable, secure, and cost-effective cloud storage.
Integrate Buffalo TeraStation NAS with IDrive® e2 employing a scalable, secure, and cost-effective cloud storage.
Use IDrive® e2 to speed up your content delivery with bunny.net.
Integrate Caringo Swarm with IDrive® e2 to manage unstructured data with a secure, scalable cloud storage.
Integrate Catalogic DPX vPlus with IDrive® e2 to use capable, scalable cloud object storage for secure backups and recovery.
Synchronize/backup Mac data with ChronoSync and access via IDrive® e2.
Integrate ClickHouse DBMS with IDrive® e2 to power large-scale analytics with a scalable, secure cloud object storage.
Integrate CloudBackO with IDrive® e2 using a scalable, secure, and cost-effective cloud storage.
Integrate CloudBerry Explorer for Mac with IDrive® e2 to manage files across local and cloud storage.
Integrate Cloud IBR with IDrive® e2 to enable scalable, secure, and efficient disaster recovery management.
Integrate Cloudron with IDrive® e2 to simplify self-hosting, ensure backups, and manage apps with secure cloud storage.
Integrate Cloudsfer with IDrive® e2 to simplify secure data migration, backup, and sync across cloud and on-premises.
Cloud object storage solution ideal for use with Cohesity DataProtect.
Integrate NetBackup Client Backup with IDrive® e2 for systematic integration with secure, scalable cloud storage.
Integrate Couchdrop with IDrive® e2 for secure, automated file transfers and workflows across protocols and storage.
Integrate Cloudmounter with IDrive® e2 to store and manage files in a single place.
Access and manage your IDrive® e2 cloud storage via Cloudflare.
Whitelabeled, high performing backup solution for IT providers.
Integrate Commander One with IDrive® e2 to manage files and systematize operations with secure cloud object storage.
Use Commvault to backup your data to IDrive® e2 cloud storage.
Integrate Commvault Cloud with IDrive® e2 for scalable cloud object storage that supports secure backups and fast recovery.
Upload and restore Couchbase Files to IDrive® e2 with ease.
Back up your websites and servers using IDrive® e2 with cPanel for reliable and secure additional storage options.
Configure CrossFTP with IDrive® e2 hot cloud storage to speed up your uploads and downloads.
Integrate CTERA with IDrive® e2 to extend secure file services and backup using scalable, reliable cloud object storage.
Store data with IDrive® e2 and collaborate in real-time using the CuttingRoom video editor.
Backup your Microsoft 365 data, shared drive, website data, contacts, and calendar locally or to IDrive® e2 hot cloud storage.
Access and manage your IDrive® e2 cloud storage using a Cyberduck connection.
Integrate Dalet Flex with IDrive® e2 to optimize media workflows and distribution with scalable, secure storage.
Integrate DataCore vFilO with IDrive® e2 to unify hybrid, multi-cloud file and object storage with a scalable object storage.
Dell PowerProtect Data Domain's Cloud Tier supports IDrive® e2 hot Cloud Storage for standard-infrequent-access storage classes.
Integrate Dell's ClarityNow with IDrive® e2 to optimize data analysis, and tiered storage with scalable object storage.
Integrate Diskover with IDrive® e2 to unify data visibility and control with scalable, secure cloud storage.
Integrate DobiMigrate with IDrive® e2 to execute fast, automated, large-scale data migrations with secure cloud storage.
Integrate DobiProtect with IDrive® e2 to manage, and recover unstructured data using scalable cloud object storage.
Integrate DragonDisk with IDrive® e2 to manage backups and file transfers using a cost-effective cloud object storage.
Upload files to IDrive® e2 Hot Cloud Storage and share it easily with anyone.
Integrate Dropzone with IDrive® e2 to simplify transfers, automate workflows, and extend drag-and-drop to the cloud.
Backup your computers with Duplicacy and store the data in an IDrive® e2 bucket.
Store, access, and manage your data backups on IDrive® e2 via Duplicati.
Use IDrive® e2 to store EditShare FLEX Sync data affordably and securely.
Integrate eMAM with IDrive® e2 to streamline media management, archiving, and collaboration using scalable cloud object storage.
Integrate EVO shared storage by SNS with IDrive® e2 for scalable, secure, efficient media workflow and collaboration.
Use the cloud storage as an external drive to store data from these applications.
Integrate FalconStor with IDrive® e2 to enable disaster recovery, and hybrid cloud protection with a scalable storage.
Use Fastly CDN as a front end for your public bucket and improve user experience.
Integrate FileBrowser with IDrive® e2 to manage file access and sharing with a capable, scalable object storage.
Integrating FileCloud with IDrive® e2 facilitates a scalable, secure cloud object storage for off-site file management.
Upload files to IDrive® e2 Hot Cloud Storage and manage file transfer workload.
Seamlessly transfer files from your IDrive® e2 Cloud Storage with Filezilla Pro.
Integrate FineUploader with IDrive® e2 for capable, scalable cloud object storage to simplify direct-to-cloud uploads.
Use Flexify.IO to transfer data from your Amazon S3 buckets to IDrive® e2.
Integrate Fog.io with IDrive® e2 to manage Ruby cloud resources using a scalable, secure object storage solution.
Integrate ForkLift with IDrive® e2 for systematic file management with a scalable, secure cloud object storage.
Integrate GB Labs Unify with IDrive® e2 to enable unified media workflows on scalable, high-performance cloud storage.
Mount your IDrive® e2 bucket on your Linux machines with GeeseFS.
Backup and sync to and from your IDrive® e2 cloud storage.
Integrate Goofys with IDrive® e2 to enable scalable and secure access to cloud object storage for extensive workloads.
Integrate GS RichCopy 360 with IDrive® e2 for secure, automated file migration and sync with a scalable object storage.
Use IDrive® e2 Cloud Storage with Hammerspace as a storage volume to read and write data.
Integrate Handy Backup with IDrive® e2 to backup local files and folders to the cloud, enhancing data protection.
Integrate HashBackup with IDrive® e2 to enable secure, deduplicated, and encrypted backups with scalable cloud object storage.
Upload media files to IDrive® e2 Hot Cloud Storage and manage media workflow.
Integrate Hiscale FLICS with IDrive® e2 to enable scalable video transcoding with secure, efficient cloud object storage.
Integrate Hiscale JOBS with IDrive® e2 to organize video workflows using scalable, secure, and cost-effective cloud object storage.
Integrate Hitachi HCP CloudScale Platform with IDrive® e2 for efficient object data tiering.
Integrate Hitachi Content Platform (HCP) with IDrive® e2 to optimize unstructured data management using scalable cloud object storage.
Integrate HYCU with IDrive® e2 to enable secure and efficient data protection with scalable cloud object storage.
iconik is a media asset management tool makes easy to organize, search, and work with your files stored on IDrive® e2.
Use Iperius to backup your data to IDrive® e2 hot cloud storage.
Store your iRODS data in IDrive® e2 cloud object storage
Use IDrive® e2 as a reliable storage destination for your JetBackup5.
Integrate Joplin with IDrive® e2 to sync, secure, and manage notes while utilizing a scalable cloud object storage.
Integrate Kopia Backup with IDrive® e2 to enable secure, scalable cloud object storage for encrypted snapshot backups.
Integrate LakeFS with IDrive® e2 to enable scalable, efficient cloud storage with controlled data versioning.
Integrate Leonovus SmartFiler with IDrive® e2 to optimize storage, reduce costs, and utilize a scalable cloud object storage.
Store your LucidLink filespace data in IDrive® e2 securely.
Integrate Marquis Project Parking with IDrive® e2 for efficient project portability using a scalable cloud object storage.
Integrate Marquis Workspace Backup with IDrive® e2 to facilitate a scalable cloud object storage for media continuity.
Integrate Media Cloud with IDrive® e2 to offload media, enhance site performance, and utilize a scalable cloud object storage.
Integrate Media Cloud Sync with IDrive® e2 to utilize an efficient cloud object storage for optimized media management.
Integrate Mediaflex with IDrive® e2 to enable efficient content management with a capable, scalable cloud object storage.
Integrate Mediaflux with IDrive® e2 to unify and manage complex data environments using a scalable cloud object storage.
Integrate MicroFocus Data Protector with IDrive® e2 to enable secure, efficient, and scalable cloud-based backup and recovery.
Integrate Microlite BackupEDGE with IDrive® e2 for secure, efficient data protection using a scalable cloud object storage.
Stream videos to the cloud with low-latency using IDrive® e2 with Milestone XProtect.
Integrate Moonwalk with IDrive® e2 to automate data movement, reduce storage costs, and utilize scalable cloud object storage.
Mount your IDrive® e2 cloud storage as a local disk with Mountain Duck.
Use MultCloud to directly transfer, sync, and backup your data stored on IDrive® e2 accounts.
Connect to cloud object storage as a local drive.
Use NAKIVO to send backups of VMs and physical machines to your IDrive® e2 cloud account.
Integrate NetDrive with IDrive® e2 to enable secure and efficient file management using scalable cloud object storage.
Use IDrive® e2 to backup your ReadyNAS data in an offsite location, for enhanced security and availability.
Integrate Network Optix NX with IDrive® e2 to enable scalable, secure, and cost-effective video storage and management.
Access IDrive® e2 Storage with transparency and optimum productivity.
Offload your WordPress media to IDrive® e2 with Next3 Offload and speed up websites.
Use NirvaShare to share your files/folders stored on IDrive® e2 hot cloud storage with external users with ease.
Connect to NovaBACKUP via IDrive® e2 and offer backup and DRaaS.
Integrate ObjectiveFS with IDrive® e2 to deliver scalable, secure, and high-performance cloud object storage for enterprise data.
Use odrive to access IDrive® e2 and other cloud storage from one platform.
Integrate OpenDrives Atlas with IDrive® e2 to enable scalable, secure, and efficient cloud data management.
Integrate ownCloud with IDrive® e2 to enable secure file collaboration while utilizing a scalable cloud object storage.
Photos+ is an iOS app that lets you store your photos in IDrive® e2 cloud object storage.
Integrate Plesk Server with IDrive® e2 to enable secure, scalable, and efficient cloud-based data backup and storage management.
Integrate Proxmox Backup Server with IDrive® e2 for reliable protection of VMs, along with scalable cloud storage.
Integrate Pterodactyl Panel with IDrive® e2 to enable scalable and efficient game server data storage and management.
Integrate Peer Global File Service with IDrive® e2 to enable real-time file replication using scalable, secure cloud object storage.
Integrate Pulse-IT and Automate-IT with IDrive® e2 to enable secure, efficient, and scalable media workflow automation.
Backup your files from Pure Storage FlashBlade device in the affordable IDrive® e2 hot cloud storage.
Integrate PyTorch with IDrive® e2 to scale AI training and deployment using secure, cost-effective cloud object storage.
Access and manage the data in your qBackup account with IDrive® e2 Storage.
Integrate Qencode with IDrive® e2 to enable scalable and efficient video processing, storage, and global content delivery.
Backup your QNAP NAS devices with IDrive® e2 via QNAP Backup.
Integrate QScan with IDrive® e2 to automate media quality control using a scalable and efficient cloud object storage.
Use Quest Rapid Recovery with IDrive® e2 to connect to the cloud for data archiving and rapid disaster recovery.
Sync your backed up data from IDrive® e2 cloud storage to rclone.
Use Restic with IDrive® e2 to backup your Linux, BSD, Mac, and Windows systems to various storage options.
Secure your Retrospect backup, archive, and clone with
IDrive® e2 Storage.
Integrate Ross Primestream with IDrive® e2 to enable a scalable and efficient cloud storage for media asset management.
Integrate Rubrik's NAS Cloud Direct with IDrive® e2 to enable a scalable cloud storage for data protection and recovery.
Use this Windows client to manage the files stored in your IDrive® e2 buckets.
Upload or download data on IDrive® e2 hot cloud storage.
Use this solution with IDrive® e2 for seamless data storage, and secure access to data.
Integrate S3Express Command Line Utility with IDrive® e2 to add a scalable cloud storage for fast and reliable file automation.
Integrate S3QL with IDrive® e2 to add scalable cloud storage for secure backups and efficient file system workflows.
Integrate S4cmd with IDrive® e2 to accelerate file operations and add scalable cloud object storage for automated workflows.
Use with IDrive® e2 to speed up your downloads and uploads with higher-throughput transfers.
Access IDrive® e2 buckets as a local filesystem with this client.
Access your cloud data on IDrive® e2 securely using the SFTPCloud service.
Connect IDrive® e2 cloud storage with SimpleBackups and secure the data from your server,band cloud storage.
Create a Snowflake External Table and use it to reference data residing in IDrive®e2.
Integrate StorReduce with IDrive® e2 to enable efficient, secure, and scalable cloud-based data deduplication and management.
Use SyncBackPro to backup your Windows and Windows Servers to IDrive® e2 hot cloud storage with ease.
Access, manage, and backup files on IDrive® e2 Cloud Storage via Syncovery.
Use Synology Cloud Sync to synchronize your local NAS data with public cloud or on-premises storage.
Backup your Synology NAS devices with IDrive® e2 via Hyper Backup.
Integrate TNTDrive with IDrive® e2 to mount scalable, S3-compatible cloud storage as secure local Windows drives.
Manage files on your IDrive® e2 account using the Transmit's 'dual-pane'.
Integrate Trilio for Kubernetes with IDrive® e2 to enable scalable, efficient backup storage for Kubernetes workloads.
Integrate TrueNAS with IDrive® e2 to deliver on-prem storage with efficient object storage for backup and retention.
Use UpdraftPlus with IDrive® e2 to easily backup your WordPress site.
Send video data to the cloud or encode stored video data by integrating Vantage Gateway to IDrive® e2.
Integrate VAST Data with IDrive® e2 for scalable cloud object storage that supports AI workloads and large datasets.
Backup all your data to a single platform with Vembu BDR Suite and IDrive® e2 integration.
Integrate WebDrive with IDrive® e2 to enable secure, flexible, and cost-effective file access using scalable cloud object storage.
Integrate Weka.io with IDrive® e2 for capable, scalable object storage supporting high-throughput AI and parallel workloads.
Access, share, and manage files directly from your We.Team workspace using IDrive® e2 buckets and credentials.
Access and manage your IDrive® e2 buckets using WinSCP.
Integrate XenData Gateway with IDrive® e2 for scalable cloud object storage with local tiering for hybrid file workflows.
Configure XOPERO ONE to backup devices and data to IDrive® e2 S3-compatible cloud storage for scalable, and reliable protection.
Integrate Yarkon S3 with IDrive® e2 to utilize a scalable cloud object storage for secure, efficient S3 file management.
Integrate Zerto (HPE) with IDrive® e2 to add capable, scalable cloud object storage for resilient data protection and recovery.
Integrate Zmanda Pro with IDrive® e2 to add scalable and efficient cloud storage for secure, flexible enterprise backups.
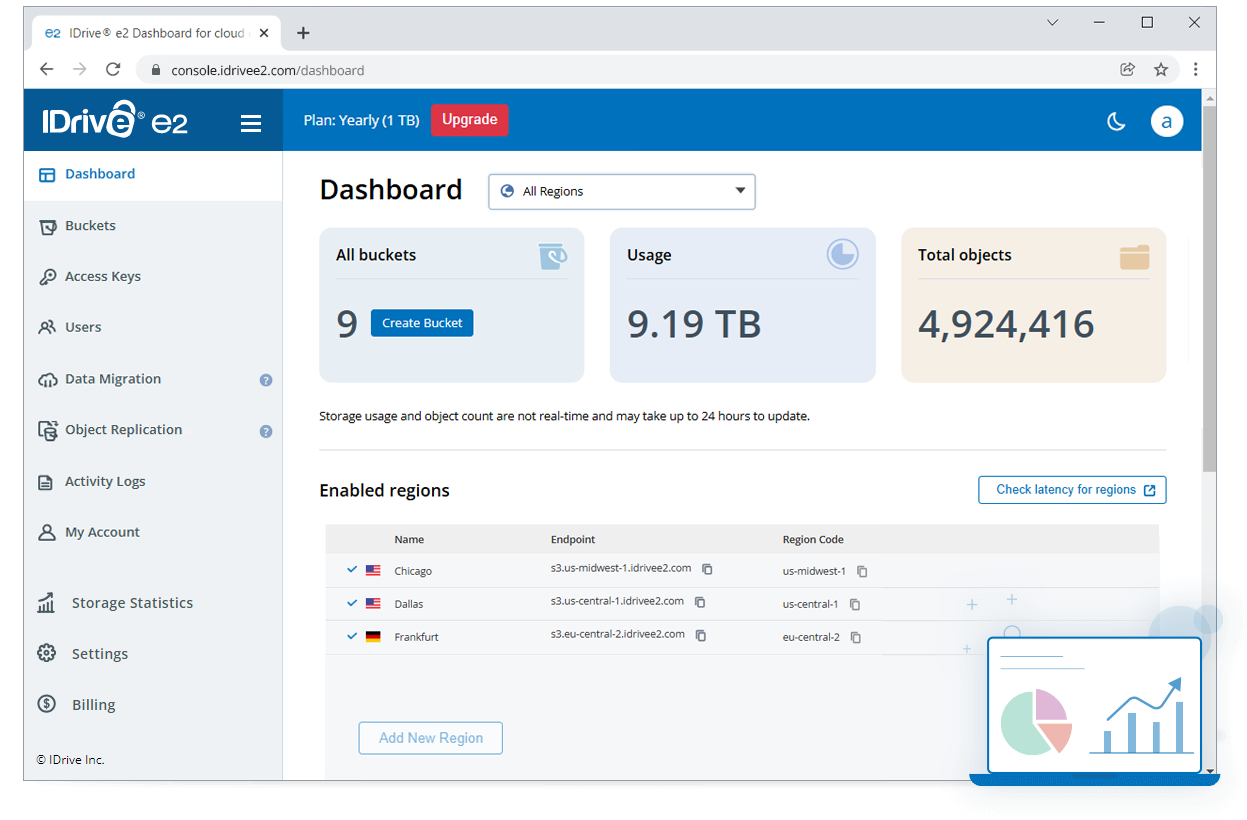
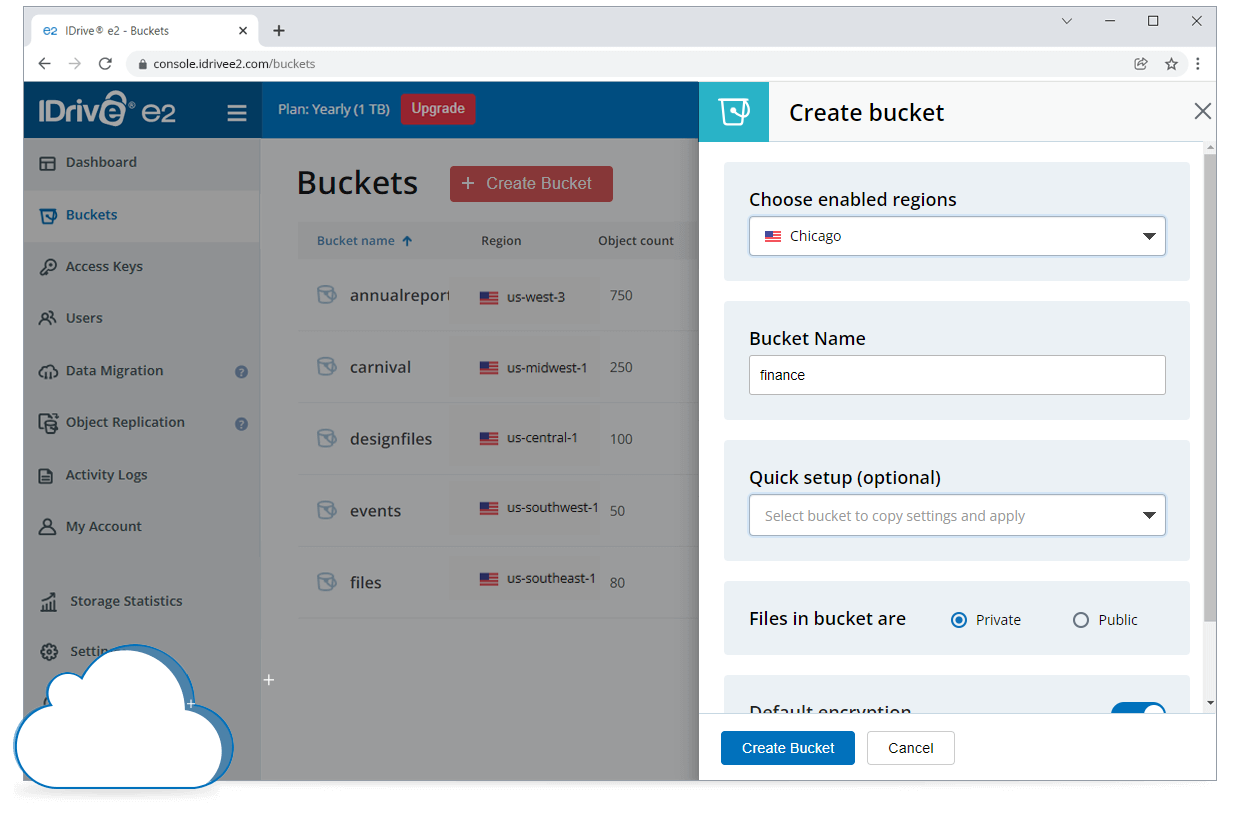
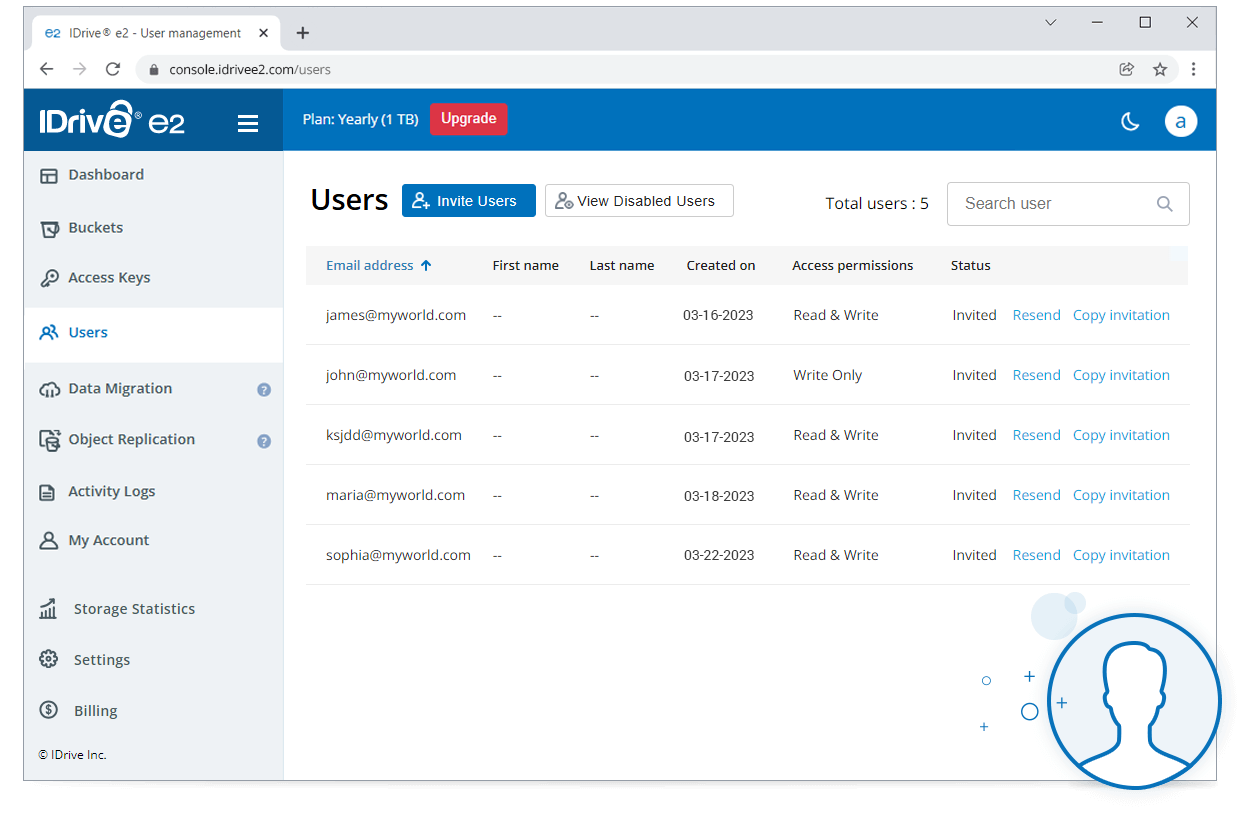
An overview of the IDrive® e2 web console
IDrive® Cloud Applications Backup
Microsoft Office 365 Backup
Secure your Microsoft applications data residing on OneDrive, Exchange, SharePoint, and Teams with reliable automated backup and granular restore.
Google Workspace Backup
Protect your Google apps data including Gmail, Drive, Calendar, and Contacts from accidental and malicious loss with daily incremental backups and quick restores.
Backup for Dropbox
Daily automated incremental backups for your Dropbox personal and professional files. Access and restore your data anytime and protect it from ransomware and more.
Box Backup
Protect your personal and business Box Drive data with automatic cloud backup, granular, and snapshot-based restore for ransomware protection.